WHAT WE DO
IT Procurement & Design Principles
It is imperative for organisations to get the initial design and architecture of a complex IT project right first time and ensure any given solution is fit-for-purpose and sits in line with the business strategy.
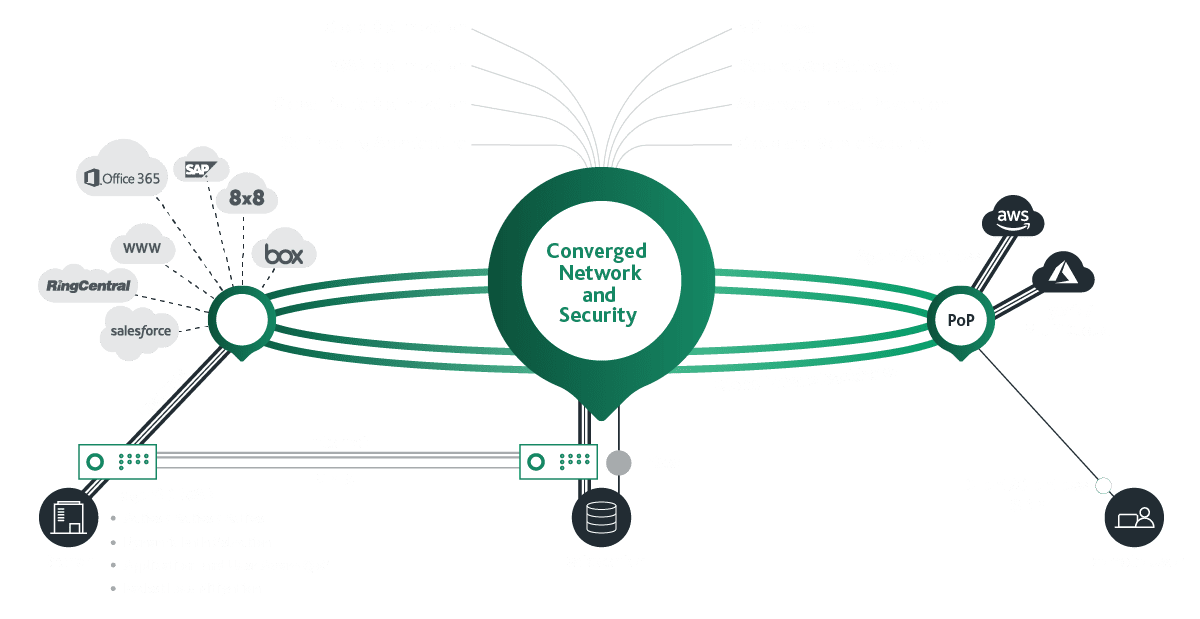
SASE SECURITY & NETWORK SERVICES
eSpida is a Cato Network partner delivering the world’s first SASE platform converging SD-WAN and network security into a global, cloud-native service. We deliver optimal network security architecture to help IT team regain control.
Open Source
Technology
Open source technology provides a platform for organisations to embrace applications, equal to and sometimes even better than mainstream applications, that can significantly contribute to the businesses IT systems.
Asset Custodianship & Life Cycle Management
By adopting an asset custodian and correct lifecycle management principles, organisations can invest proactively rather than reactively, whilst ensuring the asset quality is in line with the business needs.
Disaster Recovery & Business Continuity
DR & BC are critical strategies that every business must have in place. Its key aim is to protect the business from unforeseen incidents and to get business activity running as close to normal as possible, as quickly as possible.
Cloud
Computing
Cloud integration enables business to configure and share multiple applications in the cloud. To determine its suitability a comprehensive analysis of business’s infrastructure requirements is essential.